
The recent POODLE attack (Padding Oracle On Downgraded Legacy Encryption) exploits a vulnerability of an older version of SSL (SSLv3) by performing a padding oracle attack — and thereby allowing a man-in-the-middle scenario.
To be vulnerable, both client (browser) and server have to support SSLv3. If either one does not support or has disabled the protocol, this vulnerability cannot be exploited. This tiny article shows you how to disable SSLv3 in Firefox — thereby effectively making your browser POODLE-safe.
To check if you are vulnerable, go to “poodletest.com” (site now defunct, July 2019) and check the image of the poodle:

If the poodletest-site site shows the above image, it means you could be attacked. All you have to do to fix this issue is to tell Firefox to only use TLSv1 and above. Unfortunately, there is no option in the frontend to do that, so you have to revert to the key/value configuration. Type about:config in the browser and change the security.tls.version.min option to 1:
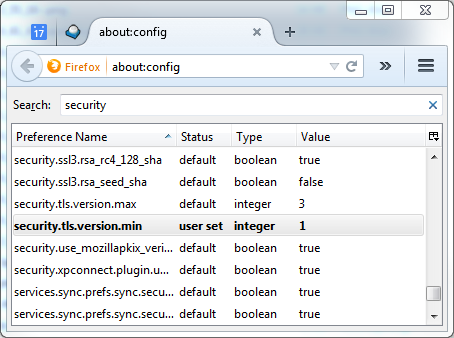
Done! After a browser restart, you’ll see that you’re not vulnerable anymore, because Firefox will not connect to sites with SSLv3 anymore:

A. About this post
I’m trying a new section for my blog. I call it Code Snippets. It’ll be very short, code-focused posts of things I recently discovered or find fascinating or helpful. I hope this helps.

Recent Comments